Add HAProxy in front of Home Assistant
Posted on 2024-17-02
HAProxy is a widely used HTTP reverse proxy and I use it at home to give access to various internal services I need. At home, I also use home assistant to manage my heaters and my aquarium. Both solutions are open source and I guess many people will use them together at some point.
Because HAProxy operates as a reverse proxy, it uses (by default) an IP address from the local machine to get connected to the server (home assistant in our case). When doing so, home assistant will see all clients coming from the same IP address. The problem is that Home assistant can be configured to block IPs which are failed too many login attempts.
Warning
This means that if HAProxy IP address got banned, then nobody will be able to use Home assistant anymore!
In order to avoid this situation, we want to properly configure HAProxy and home assistant together.
First, let's update HAProxy's configuration to send a X-Forwarded-For HTTP header which contains the end user client IP address:
backend b_homeassistant [...] http-request set-header x-forwarded-for %[src] [...]
Now, on home assistant side, just configure it to tell it there is an HAProxy in front of it and it must trust the X-Forwarded-For header sent by it:
http:
use_x_forwarded_for: true
trusted_proxies:
- 192.168.A.B # Reverse proxy / HAProxy IP address
When somebody fails on login, you'll see a notification like this:
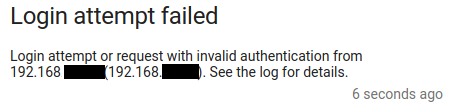
This shouldn't be the HAProxy address, but the address of the mobile phone / laptop who performed this attempt!
Get HAProxy core files on Debian 12
Posted on 2024-17-02
HAProxy is usually very reliable, that said my use case is not very common: I am using cutting edge version of the software on an aarch64 system and I may use code path that very few people uses, and so I may meet some bugs.
Note
HAProxy is Open Source and what I love the most about open source is that you can help the community making the product even better. Contributions are not only code, they may be a nice bug report that dev can leverage to quickly find the issue and make the software more reliable. This applies to any open source solution you use!
So today, we'll see how we can help the community when an unexpected event happens :)
Note
Keep in mind these instructions apply to Debian 12. They might be different for your own environment.
First, we need to raise the size for the core files. For this purpose, we create a new file in /etc/security/limits.d/core.conf:
* soft core unlimited
Then, we need to tell our kernel where to save coredump files. For this, we'll add a new file in /etc/sysctl.d/98-core.conf with the following content:
kernel.core_pattern=/tmp/core-%e-%p
Because our HAProxy is chrooted, we need to ensure that a /tmp folder exists in there:
sudo mkdir YOUR_HAPROXY_CHROOT_PATH/tmp sudo chmod a+w YOUR_HAPROXY_CHROOT_PATH/tmp
Last, we can also enable the set-dumpable parameter in HAProxy's global configuration.
global [...] set-dumpable
According to the doc, this parameter will perform the following:
will try hard to re-enable core dumps that were possibly disabled by file size limitations (ulimit -f), core size limitations (ulimit -c), or "dumpability" of a process after changing its UID/GID (such
It's basically a very nice helper, but does not prevent you from checking a core dump is well produced at the expected place: sudo kill -11 $(pgrep haproxy) will produce a core.
A quick troubleshooting / checklist if you can't get your core files: - ensure ulimit -f and ulimit -c are set properly for the user HAProxy drops privileges to - ensure the target core dump directory exists in the chroot - ensure the user running the HAProxy process can write into this directory - always try to generate a core to double check everything works as expected
For more information and use cases on this topic, you can read this excellent page
For the record, the "bug" I am tracking currently is not in HAProxy, but somewhere between OpenSSL and the libc on my aarch64 debian. Here is my backtrace from gdb:
#0 0x0000ffffa12ef690 in free () from /lib/aarch64-linux-gnu/libc.so.6
#1 0x0000aaaad8509cec in ossl_ecx_key_free ()
#2 0x0000aaaad8468f18 in ecx_freectx ()
#3 0x0000aaaad83b22c4 in evp_pkey_ctx_free_old_ops ()
#4 0x0000aaaad83b2330 in EVP_PKEY_CTX_free ()
#5 0x0000aaaad82a60dc in ssl_derive ()
#6 0x0000aaaad82edfe0 in tls_construct_stoc_key_share ()
#7 0x0000aaaad82e410c in tls_construct_extensions ()
#8 0x0000aaaad82feea4 in tls_construct_server_hello ()
#9 0x0000aaaad82ef888 in state_machine ()
#10 0x0000aaaad82b616c in SSL_do_handshake ()
#11 0x0000aaaad7f01670 in ssl_sock_handshake (conn=0xaaaadb76cb70, flag=134217728) at src/ssl_sock.c:6283
#12 0x0000aaaad7f02398 in ssl_sock_io_cb (t=0xffff8c02b7d0, context=0xffff8c02ba10, state=32960)
at src/ssl_sock.c:6626
#13 0x0000aaaad81ce300 in run_tasks_from_lists (budgets=0xffff9b7ec6d8) at src/task.c:596
#14 0x0000aaaad81cf090 in process_runnable_tasks () at src/task.c:876
#15 0x0000aaaad816e73c in run_poll_loop () at src/haproxy.c:3050
#16 0x0000aaaad816f0b4 in run_thread_poll_loop (data=0xaaaad8af3cc0 <ha_thread_info+192>) at src/haproxy.c:3252
Cross compile HAProxy 2.9 for aarch64 from x86_64 with QUIC
Posted on 2024-14-02
HAProxy is a reverse-proxy software Load-Balancer. It is very famous for its high performance and reliability. That's why we may want to run it anywhere we can.
I am the happy owner of a rock pi s device which embeds an aarch64 4 cores CPU. I could use HAProxy provided by armbian (version 2.6.12), but for my needs it's a bit old. I want to use latest revese connect feature from HAProxy in order to expose some internal services through an HAProxy running somewhere on Internet. And for this purpose I need HAProxy 2.9+. So I have to compile it.
I don't want to use this small CPU and poor microSD card to compile HAProxy, so I prefer using my old good laptop (a lenovo x230).
Because my laptop runs a x86_64 CPU, I have to cross compile to aarch64 and here is how I do it.
Note
in my case, I wrote a Makefile to automate all these commands.
First, we need to install required packages:
sudo apt-get install --yes gcc-aarch64-linux-gnu binutils-aarch64-linux-gnu
I usually have a $HOME/haproxy folder where I git clone various versions of HAProxy source code and dependency.
Now we have to prepare an OpenSSL library: - we'll use static compilation with HAProxy, so no need the share library - we'll install source files and openssl related objects into a dedicated directory: /opt/arm/openssl
cd haproxy git clone https://github.com/openssl/openssl.git git checkout -b OpenSSL_1_1_1w OpenSSL_1_1_1w make clean ./Configure linux-aarch64 CC=/usr/bin/aarch64-linux-gnu-gcc \ --prefix=/opt/arm/openssl --openssldir=/opt/arm/openssl -static no-shared make -j 4 sudo make install
Now, we're ready to compile HAProxy 2.9:
cd haproxy git clone http://git.haproxy.org/git/haproxy-2.9.git/ 2.9 make clean make -f Makefile TARGET=linux-glibc CC=/usr/bin/aarch64-linux-gnu-gcc \ USE_OPENSSL=y SSL_INC=/opt/arm/openssl/include SSL_LIB=/opt/arm/openssl/lib \ USE_LIBCRYPT= USE_PROMEX=1 USE_QUIC=1 USE_QUIC_OPENSSL_COMPAT=1 \ CPU=armv8 \ -j 4
Note
one of the limitation here is that the binary produced will not be compatible with systemd, so just use an init file.
Extend HAProxy stats page with more stats for SSL, H2 and HTTP/1.1
Posted on 2022-12-03
HAProxy is a reverse-proxy software Load-Balancer. It is very famous for its high performance and reliability. That said, it also proposes as well very strong observability features: a stats page with many counters, a very versatile log line that can be tailored and augmented to your needs, etc... Today, we'll focus on the stats page.
To enable stats page in HAProxy, add the following configuration block to a frontend or a backend section, adjusting parameters accordingly. I personally add it into a backend and use a use-backend rule to route the traffic to it.
stats enable stats uri / stats auth USERNAME:******** stats show-legends stats show-modules
The first 3 lines are pretty common. We'll focus on the last 2 ones:
- stats show-legends (documentation): enables extra information (provided as tooltips) about backend / frontend / server such as capabilities, mode, IPs.
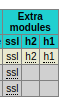
- stats show-modules (documentation): enables extra statistics for SSL, H2 and HTTP/1.1. A new column is added at the end of each line for each module. Stats are provided as tooltips.
Columns added for show-modules:
Note
stats show-legends is available since HAProxy 1.4 and stats show-modules is available since HAProxy 2.3
Make brother printer to print PDF files on modern Linux distros
Posted on 2022-04-14
For some time now, I am the happy owner of a Brother HL1210W. I like it cause it's connected to my home WiFi Network so I can store it anywhere in my house and anybody can use it. Furthermore, usually, brother support well Linux operating system...
Of course, if I am writing a quick article about it, it's because I got some issues using it under Linux laptops: everything is printed properly, but some PDFs aren't! It's not a printer issue, since the same PDF from a windows client is printed well.
Just google brother linux PDF cannot print and you will find many links speaking about this issue. If you found this page first, I will save you some time by giving you the way I fixed it!
At first, I simply installed the driver, as usual and by following brother's website recommendations. And I got stuck on my Ubuntu 20.04. Got the same issue on 3 different laptops, all of them running the same Operating System.
Then, I decided to give a try to the brother driver installation tool. Just Downloand the tool, follow the instructions, choose the right printer name and you're good!
It seems the solution was "simply" to install these packages: lib32gcc-s1 lib32stdc++6 libc6-i386 that were not installed by the default .deb printer driver package...
$ sudo bash ./linux-brprinter-installer-2.2.3-1 Input model name ->hl1210 You are going to install following packages. hl1210wlpr-3.0.1-1.i386.deb hl1210wcupswrapper-3.0.1-1.i386.deb OK? [y/N] ->y [...] The security level of AppArmor has been lowered. (aa-complain cups) aa-complain cupsd Setting /usr/sbin/cupsd to complain mode. Will you specify the Device URI? [Y/n] ->y [...] 12: lpd://brotherHL1210/BINARY_P1 select the number of destination Device URI. ->12 lpadmin -p HL1210W -v lpd://brotherHL1210/BINARY_P1 -E Test Print? [y/N] ->y wait 5s. lpr -P HL1210W /usr/share/cups/data/testprint Hit Enter/Return key.
And voilà, I can now print the PDFs I couldn't print before!